The Only Guide for Bluetooth Mouse
Table of ContentsAn Unbiased View of Bluetooth SpeakerThe 20-Second Trick For Bluetooth Keyboard7 Simple Techniques For Bluetooth MouseBluetooth Headphones Things To Know Before You Get ThisThe Buzz on Bluetooth Earbuds
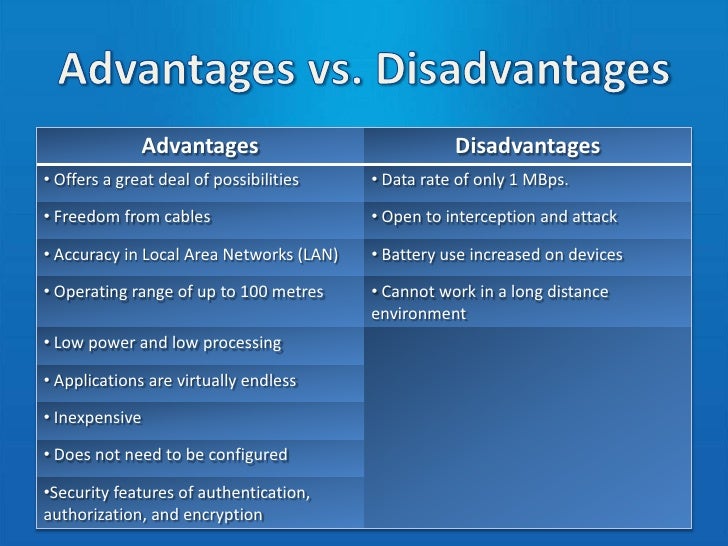
Its robust design and as much as 6 hrs of running time, makes this the ideal day-to-day noise maker.A bluetooth computer mouse is a computer mouse that utilizes radio waves to connect wirelessly with a computer system. Bluetooth mice are mobile, have an excellent range, as well as can be made use of with several gadgets. Unfortunately, bluetooth mice have not end up being rather as prominent as other bluetooth tools such as the cordless earphone because of their high prices, vulnerability to disturbance, as well as arrangement requirements.
The term "bluetooth" should always be associated with movement. Bluetooth mice can be taken virtually anywhere, placed in essentially any kind of pocket (bags, jackets, etc), as well as can be used by lots of various gadgets. Bluetooth Technology. Bluetooth computer mice likewise have a much further range than various other wireless mice. An infrared computer mouse has a "line of sight" which implies that it has to be able to in fact see the device; bluetooth computer mice do not have this trouble as they use radio waves instead of infrared lasers.
Get This Report about Bluetooth Mouse
Each device must, of course, be bluetooth-enabled and also specific tools might need different motorists. While bluetooth gadgets might be simple to make use of when they are setup and also set up, the first setup may be too intricate for some users. Most bluetooth computer mice can be arrangement by simply putting batteries in the device and turning the wireless button so that it can identify the computer in concern. https://www.twitch.tv/propairingcm.
The bluetooth computer mouse must have the ability to detect the adapter or bluetooth-enabled device immediately yet it will require to be configured by the customer. Some bluetooth devices will stroll the user via an installation wizard that will set up the computer mouse for them but some may require that the user manually enter commands into the command prompt.
Individuals with bluetooth mice do not have to bother with information burglary from hackers but they do have to manage feasible disturbance from various other bluetooth tools. For instance, if a customer has a bluetooth computer mouse with a 30 foot variety as well as there is somebody else within that 30 foot range using a bluetooth computer mouse by themselves computer system, the individual might observe that the other individual's mouse is managing the cursor on his/her computer system.
Omitting difficult installation problems as well as interference, the greatest factor that bluetooth computer mice are not extra popular is that they simply set you back more than routine as well as infrared computer mice. Bluetooth mice can set you back anywhere in between $20 and $80 depending upon where it is purchased as well as the specs that the certain computer mouse has.
The Greatest Guide To Bluetooth Technology
The question is: how protected is Bluetooth? Bluetooth is much more protected than Wi-Fi.
Now is the time to obtain up to speed up about all things Bluetooth: what it is, how it works, usual Bluetooth assaults, and also ideas for taking full advantage of Bluetooth security. What is Bluetooth?
When you attach 2 Bluetooth gadgets for the initial time, this is called. You need to approve each brand-new link, that makes Bluetooth reasonably safe and secure. When gadgets link for the very first time, the pairing is usually remembered as well as future links will occur automatically, at the very least when both devices have Bluetooth activated as well as are near each various other.
The songs you listen to, for instance, are sent out instantaneously from your Spotify app to your earphones. It's even feasible to on one network. Only one gadget, the "master," can send out information. All the various other devices, audio speakers in different locations in your home, for instance, are "receivers."Regularity Hopping, One of the excellent features of Bluetooth is that it utilizes regularity jumping.
The 6-Second Trick For Bluetooth Keyboard
Mainly it is an inconvenience, but if a recipient succumbs to such a phishing attempt and clicks on a link in among these spam messages, larger issues can arise (Bluetooth Mouse). The web link typically takes you to a web site where your personal info is swiped or malware is installed on your device.
Information like text messages, pictures, e-mails, as well as also the identifying info your device sends out to your ISP can all be stolen. Bluebugging, Below, hackers establish a surreptitious Bluetooth connection with your phone or laptop - https://businesslistingplus.com/business-listings/pro-pairing.html.
Once in, they can, and also on any apps on your device, including the applications you utilize for on the internet banking. This sort of assault is called bluebugging because it looks like the means one could bug a phone. When control over the phone is established, cybercriminals can use it to call themselves and listen in on discussions.
When you connect 2 Bluetooth devices for the initial time, this is called. You need to authorize each new connection, which makes Bluetooth fairly safe. When tools connect for the very first time, the pairing is usually kept in mind and also future connections will occur automatically, at the very least when both devices have Bluetooth triggered and also are near each various other.
Indicators on Bluetooth Mouse You Should Know

Mainly it is a nuisance, but if a recipient falls for such a phishing attempt and clicks a link in one of these spam messages, larger issues can develop. The web check over here link typically takes you to a web site where your personal information is swiped or malware is set up on your gadget.
Information like message messages, photos, e-mails, and also even the determining details your tool sends out to your ISP can all be stolen. Bluebugging, Right here, hackers establish a surreptitious Bluetooth link with your phone or laptop computer.
When in, they can, as well as also on any type of applications on your device, consisting of the applications you use for electronic banking. This sort of attack is called bluebugging since it appears like the way one could bug a phone (https://www.ottawaks.gov/profile/propairing5596/profile). When control over the phone is established, cybercriminals can utilize it to call themselves as well as listen in on conversations.